Warning
This project has been sunset and isn't being actively worked on anymore. The previously deployed services (query API, UI, discord bot) have been shut down. So the corresponding links (anonklub.xyz, docs.anonklub.xyz, query.anonklub.xyz) in docs/README(s) won't work.
AnonKlub focuses on building applications that allow for secure and anonymous proof of membership.
It does so by performing both ECDSA signatures and Merkle Tree inclusion verifications in a SNARK.
It enables privacy applications such as anonymous airdrops, anonymous NFT minting, anonymous chat groups…














| Content | Description | Status |
|---|---|---|
| discord-bot | Discord Verification Bot | ✔️ |
| nullifier | 📆 TO DO | |
| pkgs/cli | Rust CLI | ⏳ |
| pkgs/halo2-binary-merkle-tree | Binary merkle tree rust implmentation with a Halo2 gadget for merkle proof verification | ✔️ |
| pkgs/halo2-binary-merkle-tree-worker | Web worker that runs the Wasm compilation of pkgs/halo2-binary-merkle-tree | ✔️ |
| pkgs/halo2-eth-membership | Halo2 ECDSA circuit | ✔️ |
| pkgs/halo2-eth-membership-worker | Web worker that runs the Wasm compilation of pkgs/halo2-eth-membership | ✔️ |
| pkgs/merkle-tree-wasm | Merkle tree Rust crate & corresponding wasm TS package | ✔️ |
| pkgs/merkle-tree-worker | Web worker wrapper of the @anonklub/merkle-tree-wasm wasm package | ✔️ |
| pkgs/query | Node package wrapper for the Query API | ✔️ |
| pkgs/proof | Node package to assist in creating proof requests | ✔️ |
| pkgs/spartan-ecdsa-wasm | Spartan/Sapir circuits & corresponding wasm TS package. | ✔️ |
| pkgs/spartan-ecdsa-worker | Web worker wrapper of the @anonklub/spartan wasm package | ✔️ |
| queries/crypto_ethereum | Google bigquery-public-data.crypto_ethereum queries examples |
✔️ |
| queries/dune_analytics | Dune Analytics queries examples | ✔️ |
| queries/the_graph | The Graph queries examples | ✔️ |
| query-api | Query API server | ✔️ |
| ui | User Interface (fetch anonymity sets, generate or verify membership proofs) | ✔️ |
Archive branches
circom/snarkjs(groth16) implementation:archive/circomspartan-ecdsa/sapirimplementation:archive/spartan-sapir
Develop
TLDR
git clone https://github.com/anonklub/anonklub.git
cd anonklub
cp .envrc{.example,}
# edit .envrc
source .envrc
pnpm i
pnpm start.ui
Requirements
Environment
See .envrc.example.
Copy it in an .envrc file and source it.
cp .envrc{.example,}
# edit .envrc
source .envrc
Scripts
Check available scripts with pnpm run.
Especially, to start the ui or the query-api: pnpm start.ui or pnpm start.query-api.
Don't bother running build tasks explicitly beforehand: turbo takes care of topological dependencies between tasks.
Benchmarks
Overview
This benchmarking process evaluates the relationship between the parameter k and the performance metrics such as a proof generation time, proof size, and verification time. The results are stored in a CSV file and visualized using plots.
Setup
Before running the benchmarks, ensure that your Rust environment is set up correctly and that the appropriate target is configured.
Configuring the Rust Target
This benchmarking process is intended to run on a native Linux target, not on WebAssembly (WASM). The project uses a specific Rust toolchain version.
- Set Up the Rust Toolchain:
Ensure to use the same nightly Rust version in the
rust-toolchain.
[toolchain]
channel = "nightly-2024-07-25"
- Check the Installed Targets: You can check which targets are installed in your Rust toolchain with:
rustup target list --installed
- Add the Required Target:
If the
x86_64-unknown-linux-gnutarget is not installed, you can add it with:
rustup target add x86_64-unknown-linux-gnu
- Run the Benchmark: Ensure that the benchmark is run with the correct target by using the following command:
cargo test --target x86_64-unknown-linux-gnu --features "bench"
Results
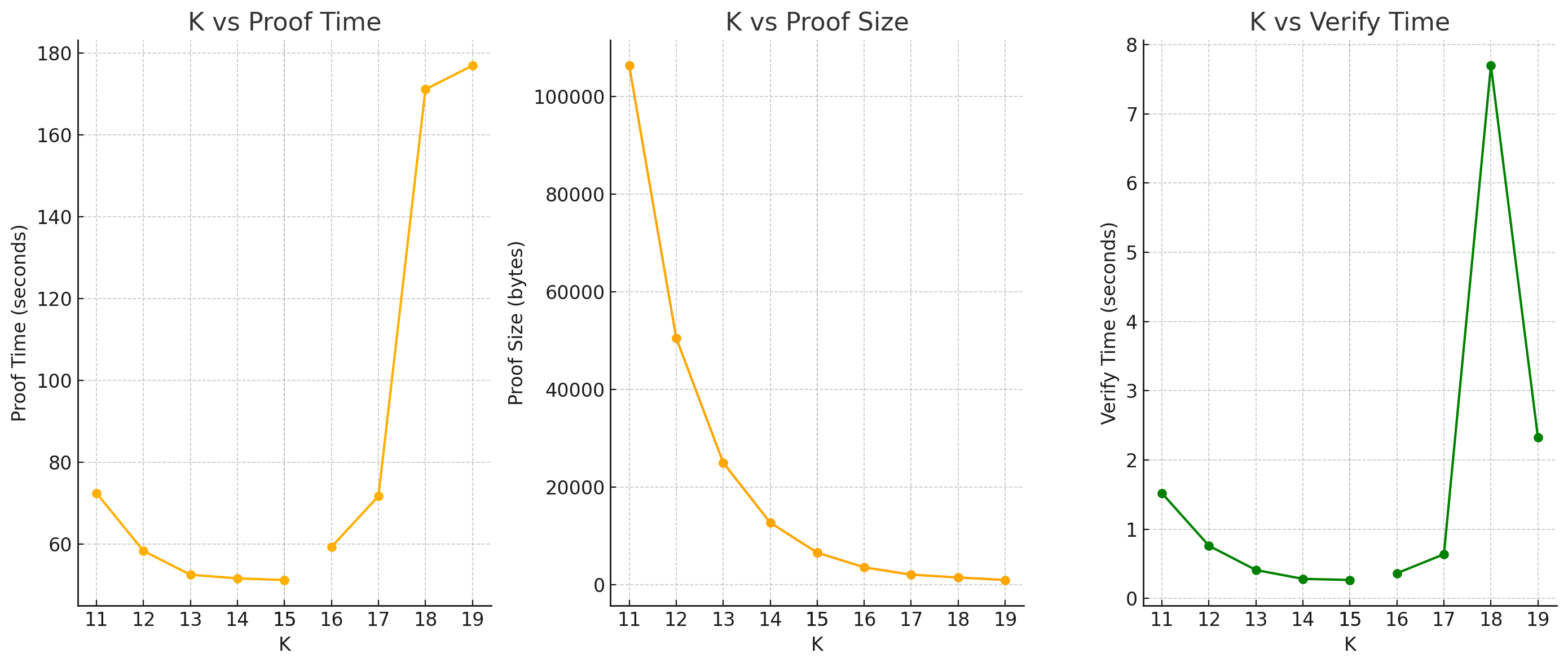
The benchmark results were obtained on Lenovo Legion 5 running Linux (12 CPU cores, 62 GB RAM) -- no GPU was used.
| k | numAdvice | numLookupAdvice | numInstance | numLookupBits | numVirtualInstance | proof_time | proof_size | verify_time |
|---|---|---|---|---|---|---|---|---|
| 19 | 1 | 1 | 1 | 18 | 1 | 176.9s | 992 | 2.3s |
| 18 | 2 | 1 | 1 | 17 | 1 | 171.1s | 1504 | 7.6s |
| 17 | 4 | 1 | 1 | 16 | 1 | 71.7s | 2080 | 639.7ms |
| 16 | 8 | 2 | 1 | 15 | 1 | 59.3s | 3584 | 365.1ms |
| 15 | 17 | 3 | 1 | 14 | 1 | 51.2s | 6592 | 267.6ms |
| 14 | 34 | 6 | 1 | 13 | 1 | 51.6s | 12736 | 283.8ms |
| 13 | 68 | 12 | 1 | 12 | 1 | 52.5s | 25024 | 411.5ms |
| 12 | 139 | 24 | 1 | 11 | 1 | 58.3s | 50528 | 761.7ms |
| 11 | 291 | 53 | 1 | 10 | 1 | 72.4s | 106304 | 1.5s |
Note: those benchmark config parameters have been selected based on
halo2-libbenchmark params github.com/axiom-crypto/halo2-lib
The benchmark results are visualized in the plot below:
Results using criterion.rs
TODO